Here’s how the 23andMe hack happened and how different login-access control solutions could have stopped it.
On Oct. 10, 2023, 23andMe announced that bad actors had stolen
This article looks at how the 23andMe hack happened and, most importantly, how various login-access control technologies could have helped 23andMe prevent this hack from happening in the first place.
How Did Hackers Break Into 23andMe?
The 23andMe hackers used “credential stuffing,” an exploit that relies on the fact that most people use the same username/password combinations on different websites. Basically, the hackers take a list of username/password combinations from another website that was hacked, and they try them out on the website they want to target.
A good example of this is the

Why Was 23andMe Vulnerable to Credential Stuffing?
According to TechCrunch:
“23andMe blamed the incident on its customers for reusing passwords, and an opt-in feature called DNA Relatives, which allows users to see the data of other opted-in users whose genetic data matches theirs. If a user had this feature turned on, in theory, it would allow hackers to scrape data on more than one user by breaking into a single user’s account.”
If you’re guilty of reusing passwords (most of us are), then you’re vulnerable to this kind of hack. But blaming the customer for bad password practices isn’t really fair. 23andMe accounts with strong passwords were also vulnerable. Because of how the “DNA Relatives” program connected user data, the accounts with weak passwords exposed those with strong passwords.
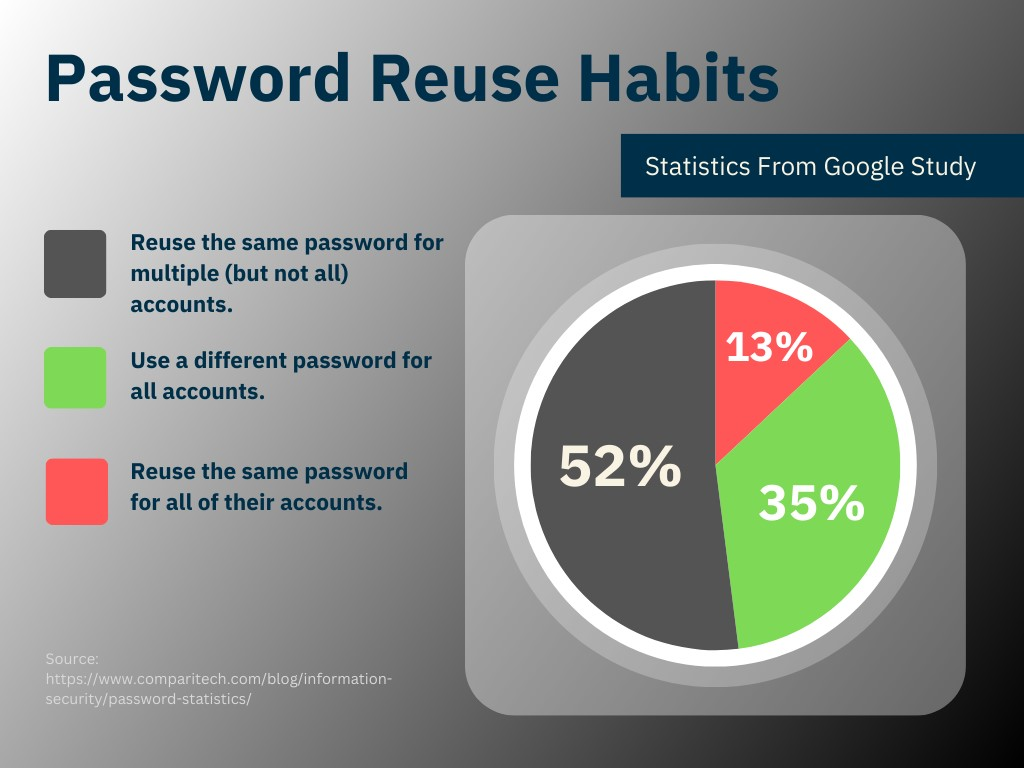
Ultimately, relying on users to adopt good password practices is a losing strategy when it comes to access control. According to recent statistics:
- 13% of people reuse the same password across all accounts (
2019 Google study) - 52% use the same for multiple accounts (
2019 Google study) - Only 35% (the responsible ones) use a different password for every account (
2019 Google study) - 81% of confirmed breaches in 2022 were due to weak, reused, or stolen passwords
(LastPass report)
Given these statistics, it’s easy to conclude that website managers
What About Password Managers Like 1Password?
Password managers offer a great solution for spinning up and keeping track of unique passwords. Most web browsers include a free password manager, and there are paid services like 1password. But you can’t force every customer to use a password manager. On social media platforms and sites like 23andMe—where customers connect and automatically share personal information—the users who fail to adopt good password practices will endanger the ones who do.
Also, password managers aren’t foolproof. If a hacker captures the master password, they get EVERYTHING. Phishing attacks—where you click a malicious link and expose your credentials—are also a problem. Dr. Siamak Shahandashti from the Department of Computer Science at the University of York highlighted these vulnerabilities in the following statement:
“Vulnerabilities in password managers provide opportunities for hackers to extract credentials, compromising commercial information or violating employee information. Because they are gatekeepers to a lot of sensitive information, rigorous security analysis of password managers is crucial.
“Our study shows that a phishing attack from a malicious app is highly feasible – if a victim is tricked into installing a malicious app it will be able to present itself as a legitimate option on the autofill prompt and have a high chance of success.”
Ultimately, password managers are better than nothing—and they can help you stay safer, but even the users with password managers were vulnerable in the 23andMe attack because of the way user accounts interconnected and shared personal information. Something more has to be done to protect account access by the websites themselves.
What About Multi-Factor Authentication (MFA)?
To increase login security, a lot of websites use multi-factor authentication (MFA). There are many types of MFA, and the most popular solutions involve sending a temporary 2-factor (2FA) passcode by text message or email, forcing users to carry out an additional yet tedious authentication step.
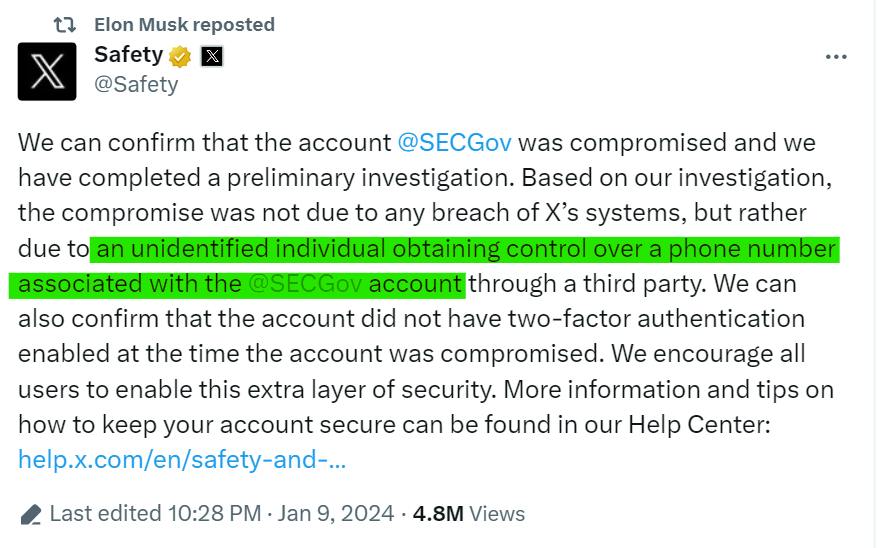
23andMe didn’t offer MFA to its users. But even if they had, text-message and email-based MFA solutions aren’t as secure as they used to be. In most cases, email is only secured by a password. Also, it’s relatively common for hackers to gain control of a smartphone through SIM swapping. In fact, this is what happened in the recent hack of the SEC’s Twitter account:
Researchers also agree that text message-based MFA is increasingly vulnerable to hacks. According to the cybersecurity firm Proofpoint:
“Contrary to what one might anticipate, there has been an increase in account takeovers among tenants that have MFA (multi-factor authentication) protection,” researchers from security firm Proofpoint said in a report. “Based on our data, at least 35% of all compromised users during the past year had MFA enabled.”
Because of these vulnerabilities, companies
“These mechanisms [text message-based 2FA strategies] are based on publicly switched telephone networks (PSTN), and I believe they’re the least secure of the MFA methods available today. That gap will only widen as MFA adoption increases attackers’ interest in breaking these methods […] It bears repeating, however, that MFA is essential – we are discussing which MFA method to use, not whether to use MFA. ”
What About Physical Security Keys Like YubiKey?

Physical security keys—such as the Yubikey from Yubico—are small devices that you connect to your phone or computer. These add an additional physical “factor” to the multifactor authentication process. Many companies, like Google, require employees to use Yubikeys when logging into their work accounts. If a user doesn’t connect the key, they can’t gain access.
Physical security keys add a powerful layer of security. However, the larger an organization gets, the more expensive these strategies become. Priced at $50 up to $105 a key, furnishing Yubikeys to every employee of a large organization is expensive. Also, the delays and management hassles of sending and replacing keys create a significant burden.
Then you have public websites—like 23andMe—with millions of users. Requiring every user of a public website or social media platform to buy a $50 hardware device is out of the question.
What About Comprehensive Security Solutions Like Cisco Duo?
Cisco Duo and other comprehensive security services offer high-quality two-factor authentication (2FA) and other authentication tools to enhance login security far beyond passwords. Users confirm access through additional steps like phone calls, push notifications, and physical security keys.
Comprehensive security services like Duo are ideal for businesses with controlled user bases. However, scaling them to work for millions of users on a website like 23andMe or Facebook wouldn’t be practical from a cost perspective.
Here’s why:
- Scaling costs: Comprehensive security services like Duo charge per user. Charging for millions of accounts wouldn’t be practical from a business perspective.
- User friction: Duo’s multi-step authentication can deter some users, especially those unfamiliar with 2FA.
- Operational complexity: Managing millions of Duo accounts requires dedicated infrastructure and resources.
What About an Authenticator App Solution Like Google Authenticator?

Mandating a 2FA solution like Google Authenticator could have been an affordable way to protect 23andMe users. However, it’s important to note that Google Authenticator comes with some important vulnerabilities:
- Phishing attacks: Attackers can create convincing fake login pages that steal usernames, passwords, and one-time codes, allowing hackers to access an account remotely.
- Social engineering: Deceptive tactics could persuade users to share their one-time codes or download malware that exposes it.
- Cloud backup vulnerability: Many users have cloud-based backups that save their authenticator keys. By compromising a cloud storage account, hackers could access this authenticator data.
- User Friction: Google Authentator requires users to download an additional app and enter a security key. Then, each time they log into the app, they need to transfer a temporary passcode from the app to the website, adding a considerable amount of hassle and friction to the login process.
- Authenticator key interception: Delivery of the authentication key code to the user is a point of vulnerability. If hackers intercept this code or obtain it somehow, the entire Google Authentication process is compromised and remote hackers can access the account from anywhere..
Despite these vulnerabilities, Google Authenticator and other authenticator apps significantly improve website login security compared to passwords alone. An authenticator system like this could have stopped the 23andMe credential-stuffing hack in its tracks.

What About Tying Access Control to the Login Device Itself, the Way Invysta Does?
There’s another solution that may have worked to prevent the 23andMe hack. This is a software-based technology from
Invysta works by detecting the unique hardware and software identifiers found in each user login device and using those identifiers to spin up an impossible-to-replicate “Anonymous Access Key.” By transforming the smartphones or laptops of 23andMe users into physical security keys, Invysta empowers websites with millions of users to highest-level access security without the need to buy or distribute an additional piece of hardware—making it impossible for remote hackers to conduct a credential stuffing attack.
Of course, Invysta is still a relatively unknown technology, and most website owners aren’t aware that it exists. In time, however, this solution could build a reputation as a powerful yet cost-effective strategy in the access control space.
Final Thoughts
This article looked at various login-access control solutions that could have helped 23andMe prevent the attack on its customers. But just because some of these solutions work today, it doesn’t mean they’ll continue to work in the future.
As we share more details about ourselves and our families online—including our DNA and ethnicity data on services like 23andMe—the continually evolving domain of digital security is more important than ever. Indeed, this isn’t just about securing our financial lives anymore. It’s about keeping our families safe from hate crimes, intimate privacy breaches, and other terrifying vulnerabilities.
As these dangers continue to increase and change in the years ahead, expect more cybersecurity solutions to appear on the market. By implementing these new technologies early, organizations may be able to avoid the financial, reputational, and physical safety damages that 23andMe has recently endured.

Jeremy Hillpot
by Jeremy Hillpot @hillpot.Jeremy Hillpot offers a unique perspective on the latest trends in cybersecurity, data, crypto, and agrotechnology.
This article is from Hackernoon. It first appeared there on 16 January 2024
![]()

