The Malicious Hack and Theft of 23andMe User Data Could Have Been Prevented: Here’s How Users and Platforms Can Stay Safe
San Clemente, California – October 10, 2023
On Oct. 10, 2023, the genetic testing service, 23andMe, confirmed that the platform was hacked, and bad actors had stolen the personal and ethnic information of millions of users. Even more shocking, the hackers were selling this data—including names, photos, locations, and genetic ancestry information of 23andMe users—on the dark web.
The attack serves as a sobering wake-up call—for everyone—that the online services we use every day are not paying enough attention to the critical problem of online access security, and it’s potentially jeopardizing our physical safety as a result.
In this article, we look at how the 23andMe hack happened; and more importantly, we explore how organizations can stop dangerous breaches like this from happening in the first place.
How Did Hackers Breach Into 23andMe

It didn’t take a computer genius to carry out the 23andMe hack. All it took was an easy-to-replicate strategy called “credential stuffing.” This exploit relies on the fact that most people use the same username/password combinations on different websites.
Here’s how credential stuffing works: Imagine someone has the same password on Gmail, Amazon, and Facebook, and the password database for one of these services gets hacked and published on the internet. A good example of this is the now-famous dark web file called the RockYou2021 database. This is a publicly available file with 8.4 billion stolen credentials from different websites.
Chances are, you have some compromised credentials on this list or another one. The Have I Been Pwned website is a free service that will check if you have been the victim of a password breach like this—so you can immediately change your affected passwords.
In the case of 23andMe, the hackers simply went down their list of compromised usernames/passwords, until they found the ones that worked. This allowed them to break into thousands of accounts and scrape the data of millions of users and their genetic connections across the site.
Next, the hackers put the data up for sale on a dark web forum in August, but 23andMe didn’t notify customers of the hack until October 10. Later, on October 24, 23andMe warned customers that a second batch of data was published on the same forum.
According to the Washington Post, “Online posts offering the data for sale in underground forums said buyers could acquire 100 profiles for $1,000 or as many as 100,000 for $100,000. The Washington Post estimates that the 23andMe breach impacted approximately 14 million accounts.
Data Breaches Aren’t Just About Money Anymore

The 23andMe hack highlights an increasingly distressing dimension of the fight for digital security: personal safety.
Today, consumers spend an average of 6 hours and 37 minutes a day on their devices (according to 2023 statistics from DataReporta). During this time, they share voice and video call data, videos, photographs, personal files, live location data, and even genetic information. Frighteningly, the 23andMe hack shows how bad actors can use this data to target specific users because of their race. They can also target users by financial status, political views, religion, and other characteristics.
For obvious reasons, securing this data has become just as important for our physical safety as locking the front doors of our homes. Nevertheless, recent statistics show that users and websites aren’t doing enough to secure their accounts. In 2023 alone, over 233 million Americans were the victims of data breaches, according to an October 2023 report from the Identity Theft Resource Center (ITRC).
Despite the dangers—and even though technology exists to prevent these attacks—numerous online services continue to rely on simple username/password strategies that leave internet users vulnerable. As discussed at the end of this article, new security technology is currently available to lock the front doors of our digital lives more securely, and this new technology is also affordable, so why are platforms leaving their users vulnerable?
Why Are Web Services So Vulnerable?
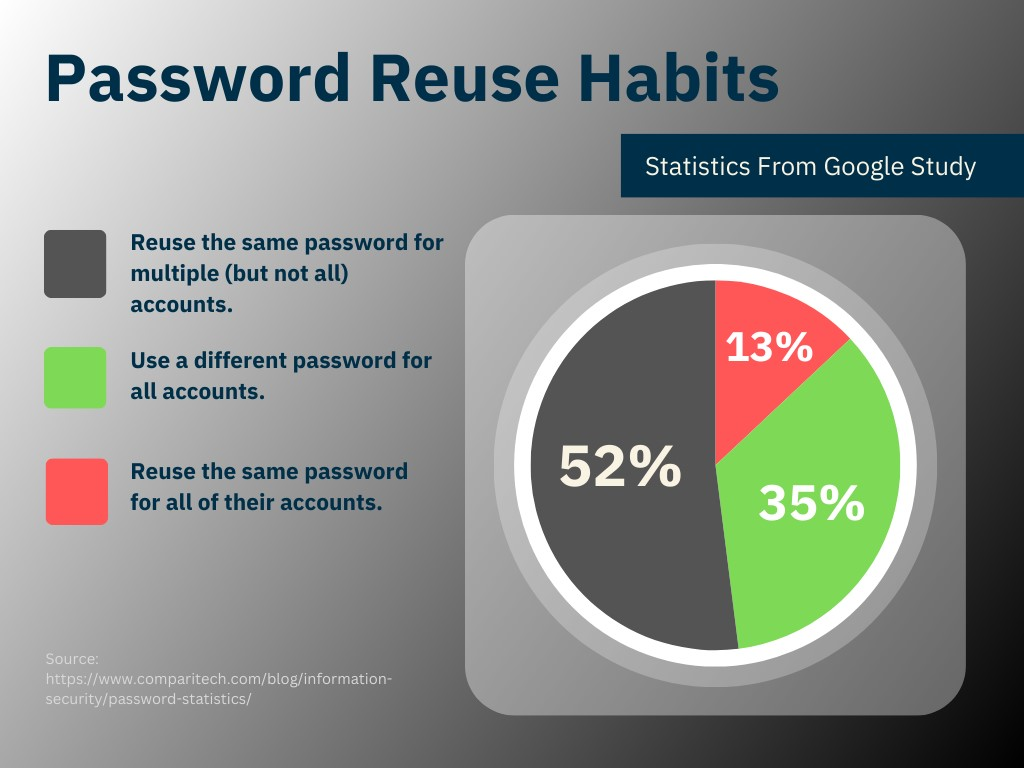
There are many reasons why internet platforms are vulnerable, but let’s consider the credential-stuffing attack on 23andMe. If you’re guilty of using the same passwords on different websites, then you’re part of the problem and vulnerable to this kind of attack (in fact most of us are). A 2019 Google study showed that 13% of people reuse the same password across all accounts, and 52% use the same for multiple accounts. Meanwhile, only 35% (the responsible ones) use a different password for every account.
Chalk it up to human nature, but—even though LastPass reported that 81% of confirmed breaches in 2022 were due to weak, reused, or stolen passwords—it’s still nearly impossible to convince and continually remind consumers to adopt better password practices. For this reason, the best way to secure online accounts is for the service providers themselves to implement better strategies.
Many websites and internet platforms already use 2-factor authentication to increase login security for their users. These solutions involve sending a temporary code by text message or email, which forces users to carry out an additional yet tedious authentication step. These 2-factor strategies help, but they aren’t as secure as they used to be.
SIM card swapping, compromised email accounts, and other hacks are rendering 2-factor authentication less and less effective every year. This is why companies like Microsoft warn against using SIM and email-based 2-factor strategies.
Fortunately, newer, higher-security login options are available, and implementing them is fast, affordable, and doesn’t complicate the login process for users. In the next section, we’ll see how one easy-to-integrate solution from Invysta Technology Group can radically increase login security for any web-based system.

How Websites and Internet Platforms Can Achieve the Highest Levels of Access Security Now
In response to increasing digital threats—like the breach that happened at 23andMe—a new 3-factor authentication technology from Invysta Technology Group offers an elegant, easy-to-implement, and highly affordable solution. Plus, it does’t have any of the fatigue, friction, and costs associated with passwords and typical two-factor (2FA) authentication strategies.
Invysta works by tying access control to the “digital DNA” of the unique login device accessing a particular account. Once set up, only registered smartphones or PCs, in the hands of approved users, can access specific accounts. Access attempts from any other devices—such as the computer of a hacker operating in another part of the world—are denied (even if the hacker has stolen the necessary login credentials).
Since Invysta is a software-based solution, deployment is instant, easy, and doesn’t require any hardware to deliver or purchase. Essentially, Invysta transforms the user’s login device into a security tool that achieves the same level of access security as a key fob solution (such as the YubiKey), without any of the delays and costs of purchasing and deploying a physical device. Best of all, Invysta works invisibly in the background. Users don’t even know it’s there.
If 23andMe had implemented Invysta’s 3-factor authentication strategy, the hackers, operating on unregistered devices, would not have been able to access user accounts via the credential stuffing technique.
Final Thoughts
As we share more details about ourselves and our families online—including the sharing of our DNA and family heritage information on services like 23andMe—digital security is growing more important than ever. This isn’t just about securing our financial lives anymore. It’s about keeping our families safe from hate crimes, intimate privacy breaches, and other terrifying vulnerabilities.
If you want to experience higher levels of safety and security on the internet, contact your favorite digital platforms, online banking services, and social media accounts. Ask them to secure your account with Invysta’s 3-factor technology for ironclad access control security!
About Invysta Technology Group
At Invysta, we are committed to revolutionizing account access security by completely eliminating the fatigue, costs, and vulnerabilities of traditional passwords and 2FA authentication strategies. Our technology provides the account login useability, reliability, and highest-level security that modern consumers, businesses, and government entities require.

